
Master Detection Engineering Through Hands-on Practice
The premier platform designed for aspiring and professional Detection Engineers.Build your Detection Engineering career by mastering SIEM rule writing, threat hunting, and log analysis. Elevate your expertise and become a world-class Detection Engineering specialist with our hands-on labs and real-world threat data.




Supports Major SIEM Query Languages





Learn Multiple Security Defense Skills Through Real-world Practice
Providing Authentic Environments and Immersive Learning Experiences to Develop Defense Architecture Capabilities
Interactive Defense Skills Training
Offering realistic interactive systems and a comprehensive blue team defense knowledge framework. Progress from point protection to complete architecture design while systematically mastering threat detection, incident response, and security operations theory to build effective enterprise security defenses.
World's First Detection Challenge Platform
Helps detection engineers practice writing detection rules, supports mainstream SIEM syntax, deepens understanding of attack behaviors through analysis of real attack logs, and allows validation of rule effectiveness using the platform's real data without needing to set up environments.
Threat Detection Collaboration
Submit your threat data and let detection experts worldwide collaborate to solve security challenges; contribute your expertise to solve detection problems others can't overcome. Here, every contribution showcases your professional capabilities.
Complete Learning System from Basic Defense Products to Enterprise Security Architecture
Each course offers real interactive systems, providing an immersive learning experience through practical exercises and interactive scenarios. From the practical use of basic enterprise security defense products to in-depth analysis of advanced threat analysis techniques, the curriculum progresses step by step. Modules are equipped with carefully designed practical problems to help students consolidate knowledge and test learning outcomes, fostering a comprehensive understanding of enterprise security architecture and ultimately mastering the professional ability to build a defense-in-depth system.
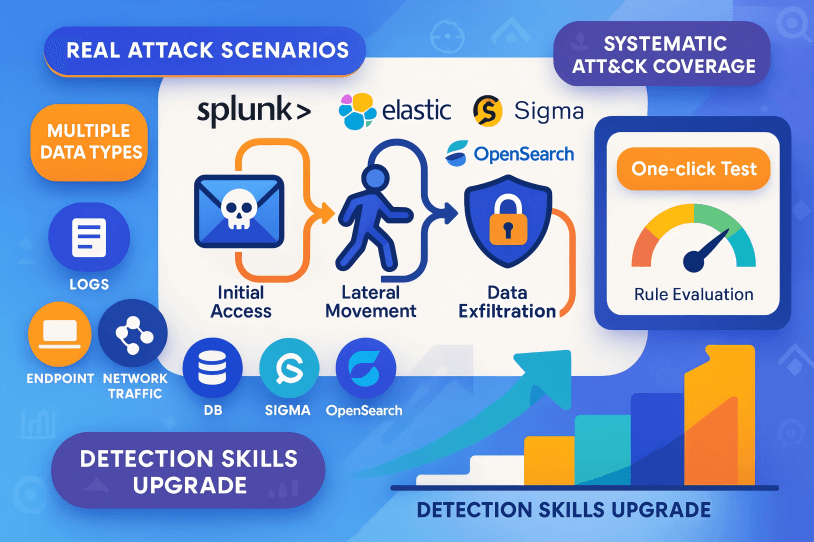
Practice Rule Writing Skills in Real Attack Scenarios
Datasets based on actual security incidents and various data types, perfectly reproducing real attack scenarios and attack chains
Support for mainstream SIEM syntax including Sigma, OpenSearch, Splunk, and Elastic
One-click testing of rule effectiveness, system evaluation of false positive rate and accuracy
Systematic coverage of modern attack techniques based on the ATT&CK framework
Step-by-step improvement of practical detection capabilities from basic detection to advanced threat hunting
Collaborative Global Threat Detection Ecosystem
In this collaborative ecosystem, you're both contributor and beneficiary. Share threat logs, solve detection challenges, or write rules that tackle security problems. Every contribution showcases your expertise and builds your reputation as a detection specialist. Join peers worldwide to create a more secure digital environment.
Pricing
Change your plant according your needs
Free
For Individuals and experiential users
$0 Per Month
Include
Everything you get in this plan
- Limited access to beginner courses
- 15-min lab runtime each session
- DetectionHub Module: 50 queries/day
Monthly Membership Best Deal
Pay for the month, suitable for all users
$9 Per Month
Include
Everything you get in this plan
- Get 30 days of membership
- Unlimited access to all courses
- 30-min lab runtime each session
- Unlimited access to all detection challenges
- DetectionHub Module: Unlimited queries
Yearly Membership
Pay for the year, suitable for all users
$89 Per Year
Include
Everything you get in this plan
- Get 1 year of membership
- Unlimited access to all courses
- 60-min lab runtime each session
- Unlimited access to all detection challenges
- DetectionHub Module: Unlimited queries
FAQ
FAQ about SOCLabs platform